 Overview
Overview
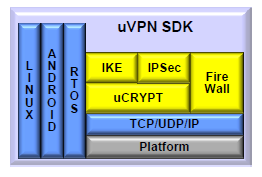 The Cypherbridge Systems VPN SDK implements IKEv1/IKEv2/IPsec for a cryptographically secure solution for IP packet networking. It provides authentication, data encryption and message integrity for embedded devices. VPN SDK is a standards based, full featured toolkit delivering system benefits including security and performance for embedded platforms, smartphones, tablets and more.
The Cypherbridge Systems VPN SDK implements IKEv1/IKEv2/IPsec for a cryptographically secure solution for IP packet networking. It provides authentication, data encryption and message integrity for embedded devices. VPN SDK is a standards based, full featured toolkit delivering system benefits including security and performance for embedded platforms, smartphones, tablets and more.
uVPN SDK Features
- IPSec Tunnel and Transport Modes
- IKEv1 and IKEv2 initiator and responder
- uCrypt library HW Crypto engine integrated
- TCP/IP stack L3 driver including LwIP support
- Integrated SPD/SAD database
- Rekey Operation
- Dead Peer Detection
- Post Quantum Ready RFC8784
- Interoperates with Strongswan, Windows IPsec VPN, Cisco, Juniper
IPsec
IPsec adds peer authentication, encryption and message integrity to IP packet networks, protecting against loss of data privacy, integrity, identity spoofing, and replay attack. IPsec adds security at the network IP layer, with no changes needed to existing client/server or streaming applications. Widely adopted, standards based and interoperable with all network equipment, IPsec can be deployed in host-to-host security channels, remote access VPN to corporate network, or network-to-network.
The VPN SDK supports AH and ESP protocols, as illustrated in the following diagram showing ESP enscapulation over a network-to-network tunneled VPN:
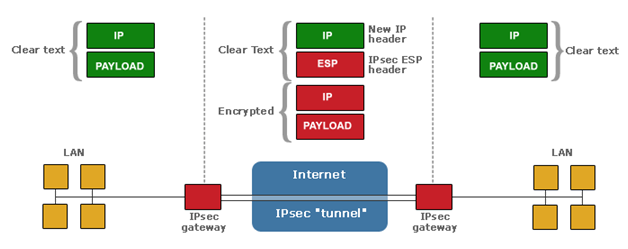 The VPN SDK is designed for both IPv4 and IPv6 operation and is optimized for deployment in embedded systems.
The VPN SDK is designed for both IPv4 and IPv6 operation and is optimized for deployment in embedded systems.
IPsec Features
- Supports AH and ESP connections
- Integrated uCrypt cryptographic library includes DHM, AES, 3DES, RC4, SHA256, SHA384, MD5
- TCP/IP interface integrates with RTOS, Kernel, User Mode TCP/IP stacks
IKE- Internet Key Exchange
VPN uIKE implements IKEv1 and IKEv2 standards based protocols to set up Security Associations (SA) for IPsec. Peer systems dynamically establish and synchronize the IKE SA through mutual authentication and secure exchange of session keys.
The SPD governs the policy and management of the security layers. The Security Policy Database (SPD) is used to define traffic flows, such that selected network traffic and direction can be configured on a granular basis. This allows all or selected network traffic to be protected with IPsec.
VPN uIKE stores the keys in the Security Association Database (SAD). IPsec fetches the cipher and authentication type and keys from the SAD, then applies security to an IP packet to encrypt outbound traffic, and decrypt inbound packets.
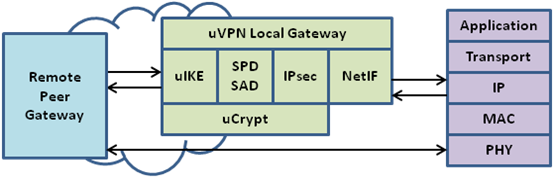
uVPN Integrated Solution
The following diagram shows the relationship between IKEv2 protocol, the SPD/SAD tables, IPsec, and the components of the embedded TCP/IP stack. The VPN SDK implements “bump-in-stack” security processing at the TCP/IP L3 datagram layer:
 IKE Features
IKE Features
- Supports embedded IKE initiator mode, Phase1 and Phase2 security association SA
- Configurable session options for Security Association negotiation
- Automatic negotiation of IKE connection
- Authentication using shared secret and RSA key pairs