IoT cybersecurity regulation is undergoing a major shift, with legislated regulation taking effect in global regions that require product compliance to enhance IoT cybersecurity to make connect connected devices more resilient against vulnerabilities and exploits, and to protect personal information.
By 2025, it is estimated that over 150K IoT devices connect to the internet every minute, and the total number of connected IoT devices will exceed 18.8 billion. As is the case with any internet connected device, IoT devices are vulnerable to remote end-point breach and lateral movement, and botnet malware injection in consumer, industrial, and enterprise deployments. Global cybersecurity regulations are driving manufacturers to add IoT cybersecurity risk assessment, monitoring and mitigation measures in new and existing products, responding to mandatory requirements and levels of enforcement which may include penalties for non-compliance. Click here to learn more about IoT cybersecurity trends and their economic impact.
EU Cyber Resilience Act

The EU Cyber Resilience Act, or EU CRA, legislation has been set in motion starting with adoption in 2024, with active timeline to interim compliance in 2026 and full compliance in 2027. The CRA requires device manufacturers selling into the EU to adopt security oriented design, and provide continuous vulnerability monitoring, incident reporting, and software updates throughout the product lifecycle, from product development to long term support and product end-of-life. All manufacturers must be able to demonstrate secure-by-design process and product compliance, risk analysis and mitigation, and be available on the market without known exploitable vulnerabilities. The CRA raises the bar to enhance the cybersecurity of products throughout the product lifecycle, and includes significant penalties for noncompliance.
Key Dates to Remember
- December 10, 2024: Cyber Resilience Act enters into force
- September 11, 2026: Reporting obligations for vulnerabilities and security incidents become applicable to new and existing products
- December 11, 2027: Full compliance with all CRA provisions required
Simplify and Streamline CRA Compliance
Manufacturers must begin CRA planning now for new product development and existing product retroactive requirements. Cypherbridge Systems works with device manufacturers for new product design, and retroactive upgrades for existing products in the market, to meet the CRA requirements, working with partners throughout the product lifecycle with technical solutions and services including:
- Cypherbridge SDKPac off-the-shelf CRA tailored software security solutions to simplify compliance, de-risk product development and deployment, and shorten time-to-market.
- Cypherbridge CDX™ Cloud Data Exchange IoT device management, device virtualization, OTA updates and event reporting with advanced fleet management options
- Vulnerability risk assessment, software and firmware image scan, SBOM, continuous monitoring, exposure severity reporting with the Cypherbridge ESAS Software Assurance SaaS
- IoT device level software kits to detect, recover and report events and incidents including alerts and email notification, including in-device OTA update transfer agent
- Cypherbridge CDX SaaS OTA Over the Air Update last-mile services and fleet management solutions for software CI/CD workflow and deployment
CRA Product Categories
The CRA regulations apply to Products with Digital Elements (PDE) that include hardware or software to directly or indirectly make a connection to a device or network, In other words, virtually any and all devices with some form of connectivity, across industry sectors and product types from consumer, industrial and enterprise. Where existing regulation applies to certain product categories, such as medical devices and automotive, those PDEs are covered by their own stricter regulation.
The CRA Annex III and IV defines product classes based on their function, purpose and product type:
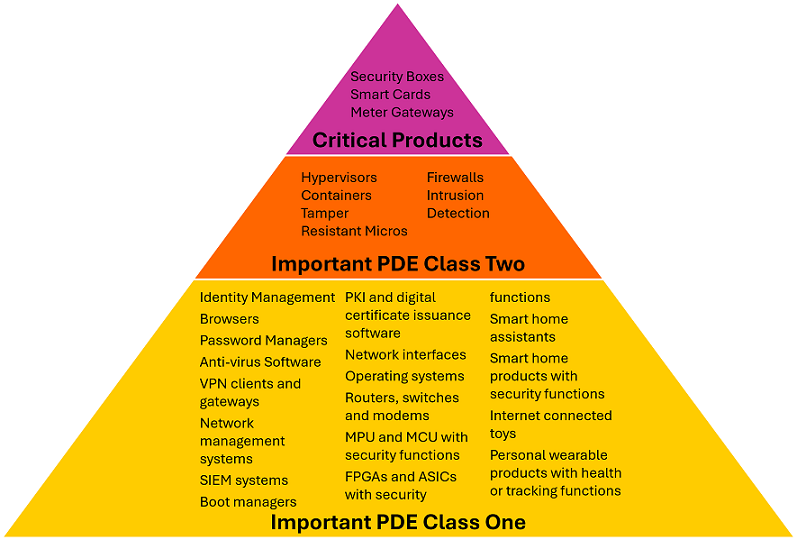
Important Products Class One
- Identity management systems
- Standalone and embedded browsers
- Password managers
- Anti-virus software
- VPN clients and gateways
- Network management systems
- Security information and event management (SIEM) systems
- Boot managers
- Public key infrastructure and digital certificate issuance software
- Physical and virtual network interfaces
- Operating systems
- Routers, modems intended for the connection to the internet, and switches
- Microprocessors and microcontrollers with security-related functionalities (MPU and MCU)
- FPGAs and ASICs with security-related functionalities
- Smart home general purpose virtual assistants
- Smart home products with security functionalities, including smart door locks, security cameras, baby monitoring systems and alarm systems
- Internet connected toys
- Personal wearable products with health monitoring or tracking functionality
Important Products Class Two
- Hypervisors and container runtime systems that support virtualised execution of operating systems
- Firewalls, intrusion detection and prevention systems
- Tamper-resistant microprocessors and microcontrollers (MPU and MCU)
Critical Products with Digital Elements
- Hardware Devices with Security Boxes
- Smart meter gateways within smart metering systems, and other devices for advanced security purposes, including secure cryptoprocessing
- Smartcards or similar devices, including secure elements
Default PDEs
All other PDEs that don’t fall into important or critical categories, are classified as Default products are PDEs, are subject to CRA regulation including process and product design, and compliance can be achieved through self-assessment.
CRA Review and Planning
Cybersecurity requires expert knowledge and best practice experience. From data-in-flight to data-at-rest, Cypherbridge delivers comprehensive solutions for your application. With our diverse SDKPac software portfolio, CRA tailored SDKPac solutions, and related services, we can help partners to design, build and deploy products meeting CRA requirements.
ESAS Software Assurance
Find out how you can level up your CRA compliance, SBOM and supply chain with vulnerability and continuous monitoring, incident reporting and mitigation response with the Cypherbridge ESAS Software Assurance Service